As the world has evolved technologically and brought so many great inventions to bring convenience to our lives, it has also brought about a whole new dimension of crimes known as cybercrimes. A network intrusion is one of these so-called virtual crimes conducted through the internet. Billions of dollars are stolen every year only by phishing attacks as disclosed by the FBI. In a world where virtual attacks have become a normal occurrence and everyone is at risk whether they are an avid internet user or someone who goes online once a day to check Facebook and emails only. Therefore, it is not recommended that you go around without proper intrusion detection and prevention systems in place. You may have subscribed to a residential internet service like Optimum internet for yourself and your family or you may be a company subscribed to a business internet service from one of the top providers. Once you are connected to the internet, you are at risk of any sort of cybercrime including intrusions.
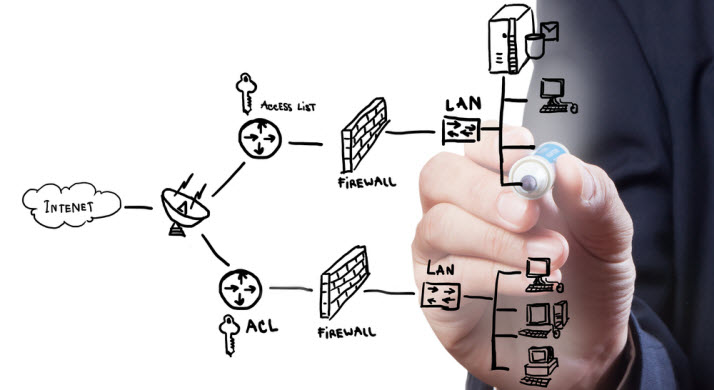
To spot intruders and hinder their malicious activity before there is any damage conducted, is what the network intrusion detection and prevention systems are used for. These systems come in both virtual and physical forms and ca scan the traffic of a network through the cloud as well as through on-premises hardware. You must read on to find out how these systems work and which ones are the top of the line for your personal and business use.
Intrusion Detection Systems
The traffic passing through your network is overseen for any signs of unusual activity through these intrusion detection and prevention systems. When it detects malicious activity, it quickly goes into action to hinder it. This would mean that the network traffic may be blocked, malicious packets may be dropped, or the connection is reset. The system would also send a notification to the administrator notifying them about the mistrustful activity detected and ended.
Generally, there are two types of detection techniques being used. The first is signature-based detection and the second is anomaly-based detection. Signature-based detection makes use of a previously distinguished dangerous activity to isolate new attacks. If the criteria of the new attack meet the one previously stored in the system it will block the exploitation right away. The downside to this type of detection, however, is that it will not identify or hinder new attacks that are different.
On the contrary, the anomaly-based detection technique proceeds to run a comparison between the recent activity and the activity it identifies as normal. If there is any sort of discrepancy spotted, it will immediately send an alert to the administrator as well as make sure the attack is prevented. This aspect is what makes this system so great since it detects new attacks as well as old ones. However, it can also notify false positives, but that easily solvable with the aid of some modern technology that makes use of artificial intelligence to determine algorithms to set a baseline of normal.
Intrusion Prevention System
There are three major types of intrusion prevention systems. Network-Based Intrusion Prevention Systems, Host-Based Intrusion Prevention Systems, and Wireless Intrusion Prevention Systems. The more widely used prevention system is the network-based prevention that works right behind the firewall. A firewall is used to block traffic coming into the network, while an IPS blocks network traffic that displays signs of a threat as per certain criteria previously stored in the memory of the system. A host-based system is built to look for dangerous activity among traffic from a particular host. Moreover, monitoring and identifying any unauthorized attempt to access a Wi-Fi network is known as wireless intrusion prevention involves.
Setting Up Network Intrusion Prevention
These systems are available as standalone network intrusion prevention systems as well as unified threat management solutions that also offer intrusion prevention as a bonus. Organizations may choose to set up whichever seems suitable for their size and usage. Another option available to users is known as a next-generation firewall that also includes an intrusion prevention system. This solution aims to cater to primarily larger organizations whereas unified threat management is meant for small to mediums sized organizations. These solutions are available as hardware as well as cloud-based whatever your preference might be. Companies choose according to their needs and preferences.
Top Intrusion Prevention Systems
Let us look into the best Intrusion Prevention Systems currently available in the market for all sorts of users.
-
McAfee Network Security Platform
The McAfee Network Security Platform defends data and systems wherever they may be, over the cloud, data centers, and even hybrid enterprise environments. It makes use of artificial intelligence to discover and block any attacks on the network and can maintain up to 32 million connections on one appliance.
-
Hillstone Network-Based Intrusion Prevention System
The Hillstone Network-Based Intrusion Prevention System offers antivirus protection, intrusion prevention, and application control, irregular behavior detection, advanced threat recognition, cloud-based security administration, cloud sandbox, and analytics performance in one appliance. It conducts in-depth packet examination and assembles inspection of all the traffic passing through the network. It can classify over 3000 applications that also include your mobile and cloud.
-
Trend Micro TippingPoint
Trend Micro’s TippingPoint can identify and discourage malicious activity as well as malware lateral movement. It guarantees the availability and pliability of your network, consequently, improving the network performance. It can be brought into instant action to screen out unwelcome and malicious traffic without entering your MAC or IP address. Its Digital Vaccine threat intelligence filters can take into account the wide-ranging vulnerability footprint instead of being focused on specific attacks. It also proposes a traffic inspection throughput of up to 120Gbps.
-
Darktrace Enterprise Immune System
The Artificial Intelligence technology used by cybersecurity, this machine possesses a learning system that learns the usage pattern of each user and device on the network. Then it uses these statistics to detect any prospective threats that may otherwise go unnoticed. The Darktrace Enterprise Immune System is not considered an Intrusion Detection and Prevention System solution and the company does not fit the category of companies providing such solutions either. However, it provides great protection, hence, the inclusion in the list.
-
Cisco Firepower Next-Generation Intrusion Prevention System
Anyone, ranging from a small workplace set-up to large businesses can use Cisco Firepower Next-Generation Intrusion Prevention System. It comes in both physical and software versions providing URL based network security as well as AMP Threat Grid integration. Offering throughput vacillating between 50Mbps to 60 Mbps, it is backed by Cisco’s Talos security research team.
Conclusion
We hope the article has served its purpose of helping you to better understand what network intrusion is and how the detection and prevention systems work. Choose wisely and venture online without any fear of violation.